INTRODUCTION
Over the past several years, the ease of copying and distributing copyrighted multimedia such as video, audio, image and software over the internet has increased significantly. With the emergence of peer-to-peer file sharing systems, this problem has only become more critical. These systems allow each PC to act as a file server for the network, sharing illegal multimedia data. As a result, there is a strong need to protect the rights of the authors and there are several possible solutions. One such solution would be cryptography which provides encryption and authentication of digital data thus enabling point to point information exchange and transactions. Yet, once the recipient validates and decrypts the data, the product can be subsequently stripped from any content identification, proof-of-ownership or other descriptive information, and further duplication and re-distribution can leave the rights holders powerless and royalty-less. Such re-distributions could have catastrophic implications for the entertainment industry, whose content has a long life span.
To overcome the problem faced in cryptography, a technology that enables some secure auxiliary information to be embedded into the original content through any channel, format or medium is made used. This is called as Digital Watermarking and could be applied to an image, an audio or a video signal.
A digital watermark is a piece of information which is embedded in the digital media and hidden in the digital content in such a way that it is inseparable from the data, this piece of information known as watermark. However, in any watermarking scheme the trade-off always exists between the robustness of the watermarking algorithm to signal processing attacks and the transparency of the watermark. It is known that as the energy of the watermark is increased, the probability of full recovery of the watermark is also increased. However, by increasing the watermark energy, we increase the noise in the signal and thus make the watermark audible.
Digital watermarking is just an adequate technology that tackles the security problems, which are not solvable by cryptography. Rooted in steganography which is the art and science of concealing the very existence of the secret message, digital watermarking provides proof and tracking capability to illicit copying and distribution of multimedia information. Which consists of three sorts of protections is needed in a secure multimedia transaction: secure communication, use contr`ol, and, a proof and tracking tool. They are complementary to protect the interests of all parties involved in a multimedia commerce transaction.
BASIC BLOCK DIAGRAM OF DIGITAL WATERMARKING FUNCTIONING
The general functioning of a typical watermark can be easily understood by means of the Fig 1. Presented below The original content (image, audio or video) is mixed with the modified version of the watermark to produce a suitable watermarked digital content at the sender’s end. At the receiving end, a normal human being perceives the image and is unable to appreciate the presence of watermark. However, a watermark detector at the receiving end extracts the encoded watermark from the content and decodes it to obtain the original watermark. In the given Fig. 1 following notations have been followed.
W = Watermark SW = Watermarked image SO= original information SO’= perceived information at the receiving end. W- Detected watermark information.
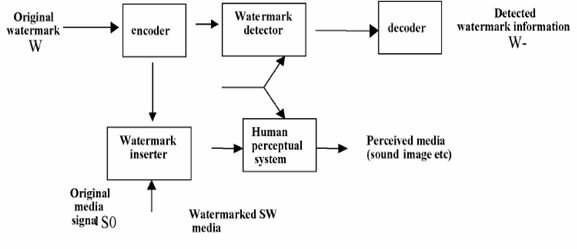
Thus the first step is to encode watermark bits into a form that will easily combine with the media data. For example in digital images, watermarks may be two dimension spatial patterns. This encoded information is then mixed with the original media content by means of watermark inserter. After insertion of the watermark also the resultant media looks similar to the original one using the peculiarities of the human visual system.
Some techniques use the principle that in eight bit gray images, changes to the least significant bit cannot be perceived by the human eye Turner. The human visual system looks at only the other seven bits thus ignoring the watermark information so the fidelity of the image is maintained. Other techniques convert the digital image into corresponding frequency domain and mix the watermark information in the high frequency part of the image. Human eye can perceive only low frequency components significantly thus ignoring the higher frequency components which are used by the watermark.
This is similar to the principle used in lossy compression as proposed by R.Schyndel. Methods using a single key are being employed but with different level of access and are termed ‘restricted key’ and ‘unrestricted key’ methods. No method using two different keys at sender and. receiver is yet known in the area of watermarking
WATERMARK CHARACTERISTICS
There are a number of important characteristics that watermarks exhibit. Some of the important ones are given below.
A. Fragility:
This is reverse of robustness. For specific applications where it is required that watermark in a text document should allow copying, but even if there is a small alteration
In text, the watermark should be destroyed. Thus if not detected, it can be ascertained that something wrong has happened with the original text. The watermarks may be designed to withstand various degrees of acceptable modifications in the watermarks on account of distortions in the media content. Here, watermark differs from a digital signature which requires a cent per cent match.
B. Tamper Resistance:
In addition to the normal signal distortions, the watermark should be resistant to distortions against the deliberate signal processing operations intended to remove the watermarks. A successful attack on a watermark system can damage or completely remove a watermark. Anticipation of such attacks and resistance against them comes in the category of tamper resistance.
C. Key restrictions:
When the keys are freely available to all detectors, it falls in the category of ‘unrestricted watermarks’ and if the key is available to a small no of detectors it comes in the category of ‘restricted watermarks’. Some watermarking methods create a unique key For each piece of data which is watermarked. Thus the owner of the data has to maintain a database of keys.
D. Fidelity:
This refers to the term imperceptible as it is referred in the literature of watermarks. The watermark should not be identified by normal viewing at the receiving end. It should also not cause any kind of perceptible distortion or deviation in the original media content. Either watermarks can be inserted into perceptually insignificant portions of the media, for example least significant bit or high frequency regions or they can also be kept in perceptually significant portions of the image using a new ‘spread spectrum technique. The second method is mostly used when robustness is the important concern.
E. Robustness:
The digital media content audio, video or digital image may undergo various kinds of distortions. Some of the common distortions are lossy compression; contrast Enhancement, alteration of colors, and modification of bass frequencies of audios, A/D or D/A conversions as well as standard geometric transformations like scaling, rotation, Cropping etc. After such distortions, the watermarks should be still present in the data and it should be possible to detect these watermarks correctly. It is proposed that watermarks exhibit robustness to deformations and distortions of image if they are placed inside the visually significant portions of the digital content rather than insignificant portions .F.Bartolini.
F. False positive rate:
In many applications, it may be required to distinguish the watermarked data from the un-watermarked data. The false positive rate of a watermark detection system is the probability that it will identify an un watermarked piece of data as containing a watermark.
G. Data Payload:
Data Payload of a watermark is the amount of information that it contains. If the watermark contains Nbits, then there are 2^N possible watermarks. Actually, there are 2^N +1 possibility because one possibility is that the watermark is not present.
H .Computational cost:
The computational cost refers to the cost of inserting and detecting watermarks in digital media content. This is very important when watermarks need to be inserted or detected in real time video or audio. The speed requirements of inserting and detecting watermarks is highly application dependent. Another important consideration while considering computational cost is scalability.
WATERMARK APPLICATION
There are a number of important applications that watermarks support; some of the important ones are given below.
A. Copy Control:
Watermark may contain information required by the Content owner that decided the policy of copying the Digital content. The information contained by the watermark may specify ‘content may not be copied’ or ‘only one copy’ etc. Subsequently, the devices used for copying the content may be required by law to contain watermark detector, which follows directives given by the content owner.
Today, many copyright infringements on the Internet occur unintentionally, resulting from Ignorance or carelessness. It is currently expensive and inconvenient to identify whether or not an image you have downloaded is copyright protected and even harder to find the correct right holders for licenses and permissions.
One of the traditional solutions is to place a visible logo or label at the corner of the image or overlay a transparent pattern over the image. Both of these methods, however, will eventually affect the quality of the image and limit the size of the message that can be placed. Moreover, they are easily tampered with.
By definition, public watermarking embeds traditional copyright notice into an image with a publicly known key or without a secret key, so that anybody can read it. Although public watermarking is not secure, it is much more difficult to remove than a visible label. Moreover, the failure of detection of the public watermark indicates that the image has been significantly tampered with and the user can be informed of the alteration.
B. Digital signatures:
Watermarks may be used to identify the owner of the content. By having this information the user may contact the owner for acquiring the legal rights to copy or using the Content.
To avoid any counterfeits being made from the source or original, multimedia works should be watermarked as early as possible. For example, the best way to protect a photographic image is to perform the ownership watermarking inside the digital camera.
Owner watermarking embeds the identifier or identifying information of the owner as well as of the multimedia work at the early phase of its creation. Since the ownership may be transferred and/or shared after creation, multiple watermarks should be allowed to identify the multiple owners in a multimedia work. A typical case is the productions of a multimedia title by compositing multiple images and other multimedia components (Audio segments, texts, video clips). Thus, both the composer and the owner of each Component want to identify their ownership in the composite work.
C. Fingerprinting:
Watermarks may be used to identify the content buyers. This may help in tracing illegal copies. When a digital media is distributed, it can contain the hidden and imperceptible information about the user, which can be detected by a watermark detector. Thus a licensed copy belonging to a specific user can be ascertained. This also resolves the possible conflicts as regards to the ownership of a digital or intellectual property. This thin is referred to as “Fingerprinting”.
Before delivering an image to the customer, the server ‘fingerprints’ the image using the customer’s identifier (such as name, or registration number) and transaction identifier(such as bill number and time).
In addition to the customer- and transaction-ID, access permissions (such as number of allowed copings) may be embedded too. The client’s rendering device will use this information to control the usage of the document.
To lighten the burden of the server, the client can also perform fingerprinting. This requires an authorized component residing in the client: whenever an image is decrypted and rendered (e.g. displayed, printed and saved as a file), the client’s identity information is embedded into this image. Recipient watermarking requires a high-speed watermark embedding process in order to accomplish a’ real-time’ online transaction. Moving the recipient watermarking from the server to the client can significantly improve the performance .referred to as “Fingerprinting”.
D. Authentication:
Watermark is used to provide authentification. It may be designed in such a way that, any possible alteration in the data either destroys the watermark or creates a mismatch between the content and the watermark that can easily be detected.
E. Broadcast monitoring:
Automatic identification of owners of data may be required to be done and used in systems responsible for monitoring the broadcasts. This may help in deciding the royalty Payments. It also helps in ensuring that commercials of a particular advertiser are played at right time and for aright duration.
F. Secret communication:
The technique of watermarking is also used in transmitting secretly information from source to destination in a hidden way. This method refers to steganography where the important or secret information may be hidden behind an image. Several public domain and shareware programs are available which use watermarking for secret communication.
thankful to your information
After browsing this, I can not help but ponder on every bit of fact. You have made your point and sent the message across completely. I am sure to keep coming back to read more.